Note: I've released a podcast of this article if you prefer.
The 20 Year Anniversary of Check Point's founding has a special place in my heart. Mostly because it is how I personally made my career. How I got involved in Information Security. How I, unbeknownst to me at the time, helped a lot of people get into Information Security.
18 years ago, I had no idea what Information Security was. I was a systems administrator working for a contracting agency fresh out of college. I did some odd programming jobs which, quite frankly, I was never that great at, and eventually, an interesting contract: doing tech support for a company out of San Mateo, CA.
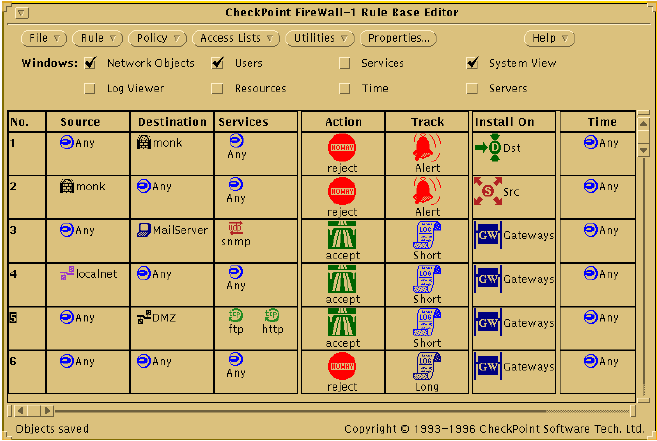
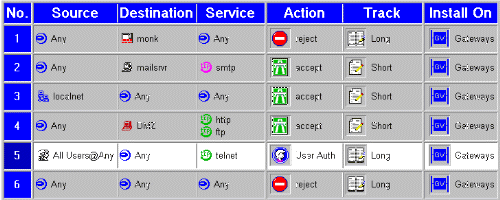
The product: Qualix HA, a high availability product for Sun Workstations based on a Veritas product. One of the products we also sold along with it and provided high availability for was a product called Check Point FireWall-1.
That contract turned into a full-time job and eventually, as the other people in the group kept getting hired out to do "professional services" or whatever, I had to learn FireWall-1 the hard way: by supporting customers calling for help without much of a backstop.
Back in those days, Check Point did all of their support out of Israel. SecureKnowledge didn't exist. They had a mailing list, which had a lot of questions asked on it, but not a lot of answers.
On a hidden page on the Qualix website, there was an FireWall-1 FAQ started by one of the developers at Qualix. I started writing entries on it. Eventually, I got permission from Qualix to take the content and put it on my website--phoneboy.com.
Qualix became Fulltime Software and got bought by Legato Systems in 1999. Before that happened, I got a job at Nokia in their IP Routing Group--the guys who make the firewall appliances that ran Check Point's firewall.
PhoneBoy's FireWall-1 FAQ existed for the better part of 8 years as a publicly available resource containing the knowledge I collected about the Check Point products from the mailing lists and my own work with the product as a technical support guy. Obviously a lot of that knowledge also migrated itself into Nokia's Knowledge Base, which I more or less maintained during my tenure there. It also made its way into two books that I published with Addison Wesley (now Pearson Education).
In parallel, I created a moderated mailing list on FireWall-1 in June of 2000, first called FireWall-1 Wizards, then renamed to FireWall-1 Gurus after the folks who own the Firewall Wizards trademark suggested I should change the name. The mailing list lasted for about 9 years.
Around 2003 or so, I started burning out. Technical Support is a difficult job to do long term in general and I had done more than my share. I ended up moving onto other things inside Nokia's Enterprise Solutions or whatever it was back at that time. In 2005, I agreed to let Barry Stiefel take the content on phoneboy.com and copy it onto cpug.org.
I kinda thought I was done with Check Point stuff by then, but I was wrong. I kept working with Nokia's Knowledgebase for the Enterprise Solutions group, which had a lot of Check Point content in it. This meant, for me, reading, writing, and re-writing this content. I kept mentoring folks in the TAC when they had issues with Check Point or just general network troubleshooting. I kept supporting other products that were somewhat Information Security related (VPN and Remote Access product as well as Sourcefire on Nokia).
When the Check Point acquisition of Nokia's Security Appliance business was announced, I wasn't sure what to expect: for a platform that I spent 10 years of my life supporting as well as my own career. When it became clearer that I had a home at Check Point, I began to start looking a bit more closely at the Check Point products again.
What I discovered was that the product hadn't changed all that much. Sure, there was NGX, the rise of Secure Platform and Check Point's own appliance offerings, and many refinements along the way, but the fundamentals of the product were basically the same.
But change was happening: I could see it before I was officially part of Check Point as I was told about the new IPS Software Blade in R70. As I started visiting the Check Point headquarters in Tel Aviv, I got to hear in more detail from the people who develop the product. I got to see the changes up close and personal. App Control, URL Filtering, Anti-Bot, the new (and old) SMB products, DLP, appliances, Gaia, I got to see it all before it was released.
Also, Check Point made a couple of key acquisitions prior to Nokia's Security Appliance business: Pointsec, which was a well-known disk encryption solution, and Zone Labs, which made the ZoneAlarm desktop firewall product. Both of which ultimately became part of Check Point's Endpoint Security offering along with the later acquired Liquid Machines to provide Document Security along with Dynasec to provide Compliance solutions to Check Point's overall product portfolio.
It's been a beautiful thing that I'm proud to say I've been a part of since nearly the beginning. And, of course, there is a lot more to come.
Let's face it: the threats to our networks have only gotten more complex, more dangerous. A lot of the fundamental issues in Information Security haven't changed, either. End Users still do unwise things. Companies don't invest enough time or money in doing the basics in security practices like segmentation, user education, changing default passwords, and a whole host of other practices.
The Information Security market has many players. Check Point plays in many spaces with different competitors in different segments but continues to grow and innovate year over year and continues to remain independent and focused on the goal of securing the Internet in a sea of acquisitions by larger, less security focused companies.
Here's to another 20 years, Check Point.