From Why Firesheep’s Time Has Come | Steve (GRC) Gibson's Blog:
In case you’ve been somewhere off the grid, and have somehow missed the news, Firesheep is an incredibly easy to use add-on for the Firefox web browser that, when invoked while connected to any open and unencrypted WiFi hotspot, lists every active web session being conducted by anyone sharing the hotspot, and allows a snooping user to hijack any other user’s online web session logon with a simple double-click of the mouse. The snooper, then logged on and impersonating the victim, can do anything the original logged on user/victim might do.
I've experimented with Firesheep on my own system. Normally, I use Google Chrome, but I installed a fresh copy of Firefox just for the occasion to try Firesheep.
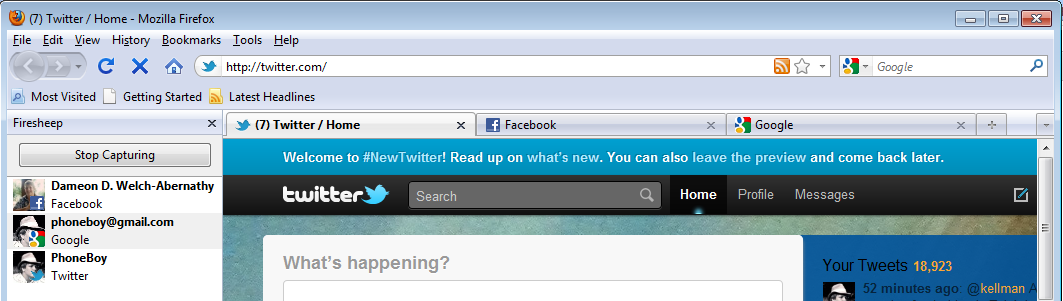
Within a few moments, I was able to pick up web sessions happening from my Google Chrome browser. I was able to use both my Facebook and Twitter from Firefox without having to log into them! It did pick up my Google login, but before I hit Gmail, I had to provide authentication. Remember, this was a fresh installation of Firefox on a machine that did not previously have Firefox installed at all!
This is scary stuff. As Steve Gibson says, though, this has always been possible with unencrypted WiFi by anyone with enough 1337 5killz to pull it off. Now, it's as simple as installing a web browser plugin.
