A lot of noise has been made recently about some nude celebrity photos that have made their way around the Internet, such as those of Jennifer Lawrence. Initially it was thought to have been a compromise of Apple's iCloud service, but, really it was because Apple failed to properly rate-limit an API that allowed rapid brute-force guessing of passwords. Apple claims it was a targeted attack on these specific users and tells users to enable two-factor authentication and use a strong password.
Getting someone's iCloud credentials, either by brute force or guessing the answers to security questions, is all well and good. It certainly explains these photos were acquired and posted. It doesn't adequately explain how supposedly deleted photos from a celebrity's iPhone were posted online.
Moti Sagey, whom I work with at Check Point, actually came up with the idea of how this might have happened. He discovered a tool called dr.fone that can "recover data from iOS devices, iCloud backup, and iTunes backup." Curious, Moti and I downloaded and installed the tool, attempting to recover data from our own iCloud backups. Lo and behold: there they were. Up to 3 iCloud backups for each device we own.
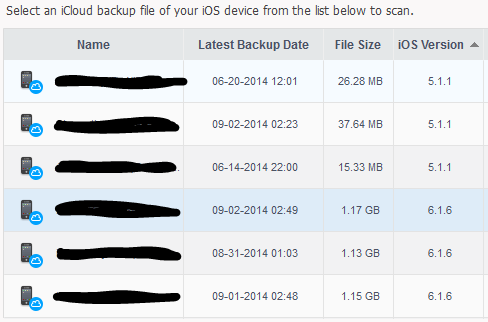
A note about the way iCloud backups work: they will only happen from your iOS device if the device is on WiFi and is plugged in--usually at night. They could also be triggered manually, but let's face it: how often do regular people do that? Almost never.
While the majority of my devices have 3 consecutive days of backups, one in particular had quite a gap in their backup dates. Which, for most celebrity-types, may be pretty common. Movie stars are like normal people: they rarely charge their phone and are rarely on WiFi outside of their own home. Given how busy some celebrities are, it doesn't seem inconceivable that they could go months without being at home on their WiFi and charging their iPhone at the same time.
What's in an iCloud backup, you ask? Quite a lot, as it turns out, including the camera roll:
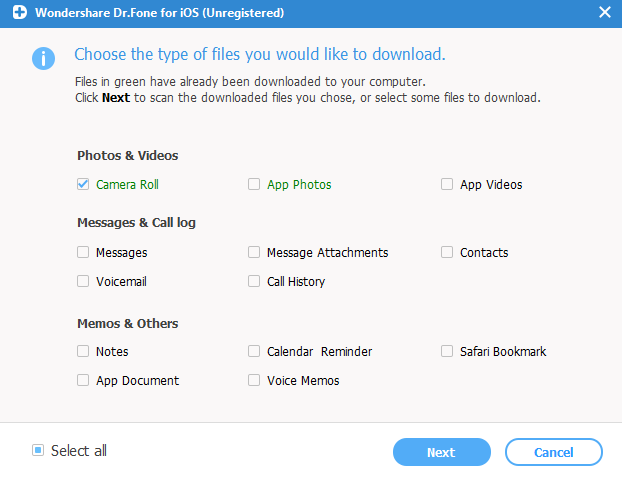
A popular celebrity with easy to guess iCloud username and password plus a rarely backed up iPhone plus a tool like dr.fone equals access to potentially naughty photos the celebrity thought were deleted months ago. Voila!
Of course, this is just the tip of the iceberg of what criminals do in order to get illicit photos and videos from celebrities, but let's be honest: why go through the trouble of social engineering, installing illicit remote access tools, and stealing authentication keys when you can take the much easier route of brute force guessing a weak password and/or easily answer their password reset questions?
People are blaming Apple here, when, last we checked, you had to opt-in to iCloud backups. Even if you choose to opt-in, you can choose what elements of your phone to back up. The fact that Apple keeps a few of them on-hand is, in fact, a good thing. Good backups are just as important as choosing a strong password or using two-factor authentication when its available. While there is some inherent risk in backing stuff up to the cloud, doing so is a greater good than never backing up your device, which is what would happen for most people without iCloud doing it for them.
Since it appears iCloud only keeps the last 3 device backups, ensuring that iCloud backs up your device regularly will also reduce the risk someone might "recover" an old nude photo you thought you deleted. Of course, if you want to reduce the risk even further, don't take the photos with your mobile phone, or at least don't do it with the default camera application. Use an ephemeral messaging app like Wickr or Telegram, at least until phones get an incognito mode similar to browsers.
Authorship Note: If Posthaven would let me mark more than one author, I would credit Moti Sagey as one. Especially since this was his idea, which I put a few refinements on.