If the security industry itself can’t be bothered to fix security issues in a timely manner, how can we expect customers to apply the patches in a timely manner? Shouldn’t we be leading by example?
Generally speaking, Check Point (where I work) is pretty quick to respond to reported issues. In some cases, fixes have been out in hours. Some of Check Point’s competitors? Not so quick. Here are a couple recent examples.
FireEye’s Year Old Vulnerability
A couple people from Check Point reported an issue to FireEye on 24 July 2014. While the issue was reported on one of their products (their ‘EX’ product), the issue actually affected several of their products. A “fixed” version of code for the product we reported on was issued on 7 July 2015, 349 days after it was first reported. This is how the issue was reported in their Q4 2015 Security Vulnerability advisory:
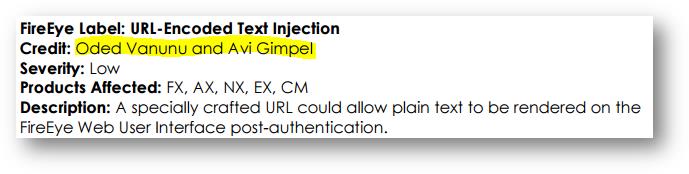
To be fair, the issue was fixed in some products in a much shorter time, but for one product, it was about 15 months.
The acknowledgement by FireEye is misleading. First of all, the employer of the reporters was not mentioned as it was for others in the advisory (it’s Check Point, as noted previously). Second of all, the actual issues reported are more serious than the somewhat misleading description FireEye chose to provide. Even with the description provided, I disagree with the “low” severity rating. Social engineering attacks, anyone?
Palo Alto Networks Evading For Three Years
I’ve largely covered the vulnerability in question on a previous post. The one update I can provide is that 3 years after the original SANS Institude paper being published highlighting the deficiencies, Palo Alto Networks finally issued an update to their Application and Threat Content that addresses the issues. Or at least they addressed the issues demonstrated by the 666 different ways to bypass Palo Alto Networks video, which are based on the same principles.
More Examples
Check Point has actually found and responsibly disclosed a number of vulnerabilities in a number of common services and software products, including those of competitors. A presentation has been posted on SlideShare providing the details.
Conclusion
Every product out there is going to have security vulnerabilities found in it, including and especially products designed to keep your environments secure. What separates the mature, market-leading vendors from the others is how you respond to such reports.
